Malware Analysis: RevShell - A Go-Based Reverse Shell
December 9th, 2025
Author's note: This report is written for the final of the TCM Security course, 'Practical Malware Analysis & Triage'.
Executive Summary
RevShell is a reverse shell malware sample first identified on xyz. It is a GoLang-compiled sample that runs on the x64 Windows Operating System. It consists of an executable, Backdoor.srvupdat.exe, which masquerades as a legitimate server update and sets up a reverse shell on the victim machine. Symptoms of infection include a blank command prompt on the victim machine, an attempt to retrieve a favicon file from an EC2 URL, frequent beacons to a command-and-control server, and continued DNS requests to local domains.
YARA signature rules are attached in Appendix A. All aforementioned indicators of compromise are listed in Appendix B. Malware sample and hashes have been submitted to VirusTotal for further examination.
Technical Summary
Upon execution, the malware creates an instance of conhost.exe, which it uses to masquerade as a legitimate system utility. It then performs a HTTP GET request to a favicon file at http[:]//ec2-3-109-20-24-srv3[.]local/favicon[.]ico, which appears to be an attempt to verify connectivity to its command-and-control server.
The malware then attempts to establish a reverse shell connection back to 10.10.1.237:3301 over TCP. If the connection is successful, the attacker can execute commands on the victim machine remotely. Regular DNS requests to local domains are also observed, likely as a means of maintaining persistence and communication with the command-and-control infrastructure.
Malware Composition
RevShell is composed of a single executable file named Backdoor.srvupdat.exe.
| File Name | File Type | File Size | MD5 Hash | SHA256 Hash | SHA1 Hash | VT Detection Ratio (as of writing) |
|---|---|---|---|---|---|---|
| Backdoor.srvupdat.exe | PE32+ executable (console) x86-64 for MS Windows | 7.29 MB | ccadd02dfee2735b574ae321fa81c654 | 914cad877a41f12bb0998bc1c28d04ee2fb33c4538707547cad726b41f7d01c3 | 5510b3eb8dfbe523946fadef2ac6dc0123e24412 | 35/72 |
Basic Static Analysis
Static analysis provides some potentially interesting strings:
http[:]//ec2-3-109-20-24-srv3[.]local/favicon[.]ico main.(*program).Start main.(*program).run main.(*program).Stop main.main .symtab Go build ID: "3RKTvI30Uc68A_c6-sMB/uAW0VxD6KHkdILq2izWY/BG7xKfK9Q2QEBRq4rzpy/NCZHQC83zX7VfgJHmlhZ" %SystemRoot%\System32\EventCreate.exe key expaH master sH97u client fH inisu]f server fH97 >socku >httpu >httpu localhosH93u 9httpu- 9Cooku AuthorizH9 Www-AuthH9 enticateH9A ;pathu1H ;secuu!f httponlyH samesiteH9
Strings such as '.symtab' and a Go build ID indicate that we are examining a GoLang binary. The use of GoLang allows for compilation across platforms and results in a statically linked binary, complicating analysis due to the inclusion of all necessary libraries within the executable itself. This is evident in the large file size and extraneous strings related to Go runtime and standard libraries. Some other strings indicate function names such as 'main.(*program).Start', which will be useful for identifying the program's entry point during dynamic analysis.
Mainly, we see the use of HTTP communication and a hardcoded URL that we will want to look out for in dynamic analysis. Other strings appear to be related to cookie handling and authorization headers, suggesting that the malware may use HTTP cookies for session management or authentication with its command-and-control server.
'EventCreate.exe' is a legitimate Windows utility used to create custom events in the Windows Event Log - we can investigate what event the malware intends to log in dynamic analysis.
Basis Dynamic Analysis
On initial execution of the malware, a blank terminal window appears, indicating that the malware is running in the background. No other initial signs of activity are observed without further tooling, and after a few seconds, the terminal window closes.
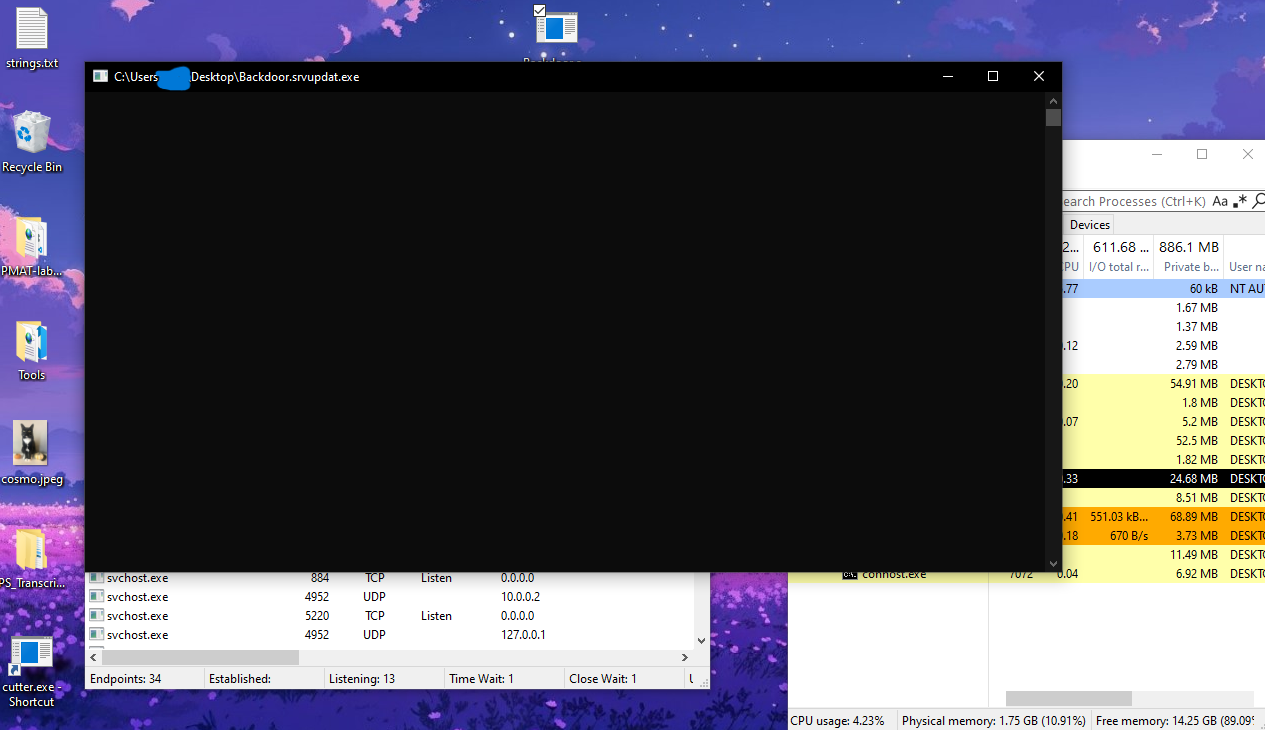
Using Procmon, it is observed that the conhost.exe is launched by the malware. The command line arguments for conhost.exe include '0xffffffff -ForceV1', which are not typical for conhost.exe. 0xffffffff indicates that there is no session attached to this console, and -ForceV1 forces conhost to launch in the legacy mode. Both of these arguments suggest that the malware is attempting to hide its console window from the user (perhaps unsuccessfully).
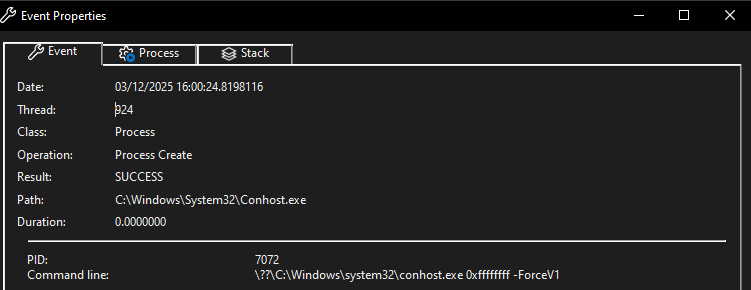
Network-based analysis with Wireshark and Procmon shows that the malware attempts to connect to the URL http[:]//ec2-3-109-20-24-srv3[.]local/favicon[.]ico using a HTTP GET request, which may be an attempt to verify connectivity to a command-and-control server. The server is no longer active, so the request fails.
Regardless of whether the connectivity attempt is successful, the malware attempts to establish a reverse shell connection to 10[.]10[.]1[.]237:3301 over TCP.
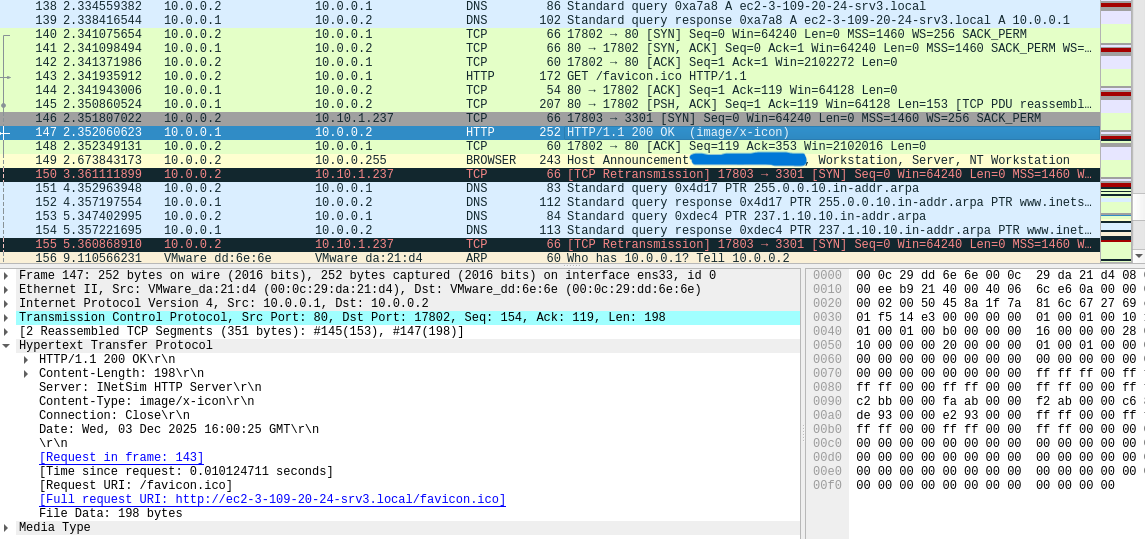
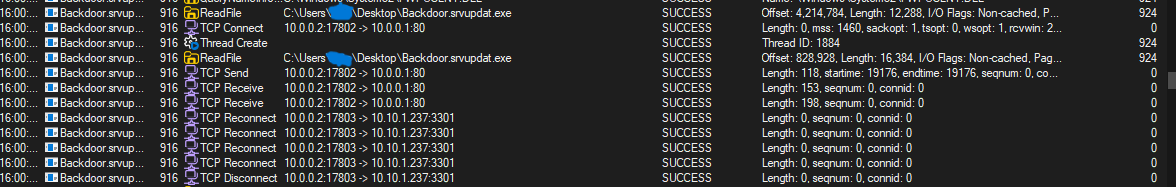
Setting up a listener on port 3301 allows for a successful reverse shell connection, allowing the command-and-control to send commands to the victim machine remotely. Requests and responses are sent unencrypted over TCP, and TCP Keep-Alive packets are sent back and forth to maintain the connection.
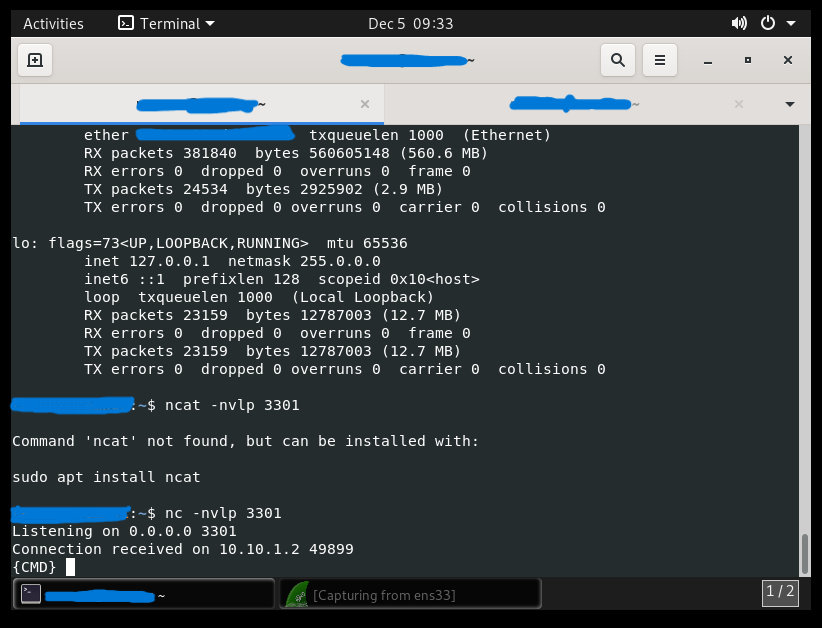
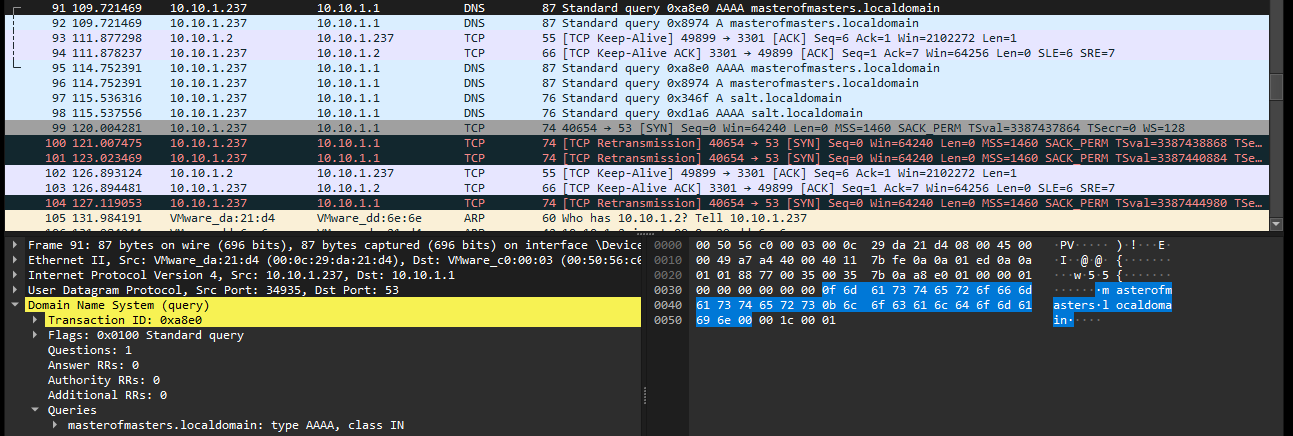
Periodic DNS requests to multiple .local domains are also observed, likely as a means of maintaining persistence and communication with the command-and-control infrastructure.
Advanced Static Analysis
Analysing Go-based malware provides some challenges as previously mentioned, which is well-discussed in this article.
Using Ghidra to decompile the binary, combined with the strings identified earlier, we can locate the main program functions. The main.program.run function appears to contain the core functionality of the malware, including the HTTP GET request to the favicon URL and the setup for the reverse shell connection. The high-level code for this section is as follows:
1) Call to a fixed URL via a HTTP GET 2) Connect to a C2 server over TCP 3) Until connection is closed: a) Read command from C2 server b) Print command locally for debugging reasons c) Execute the on the local machine and capture output d) Send the command output back to the C2
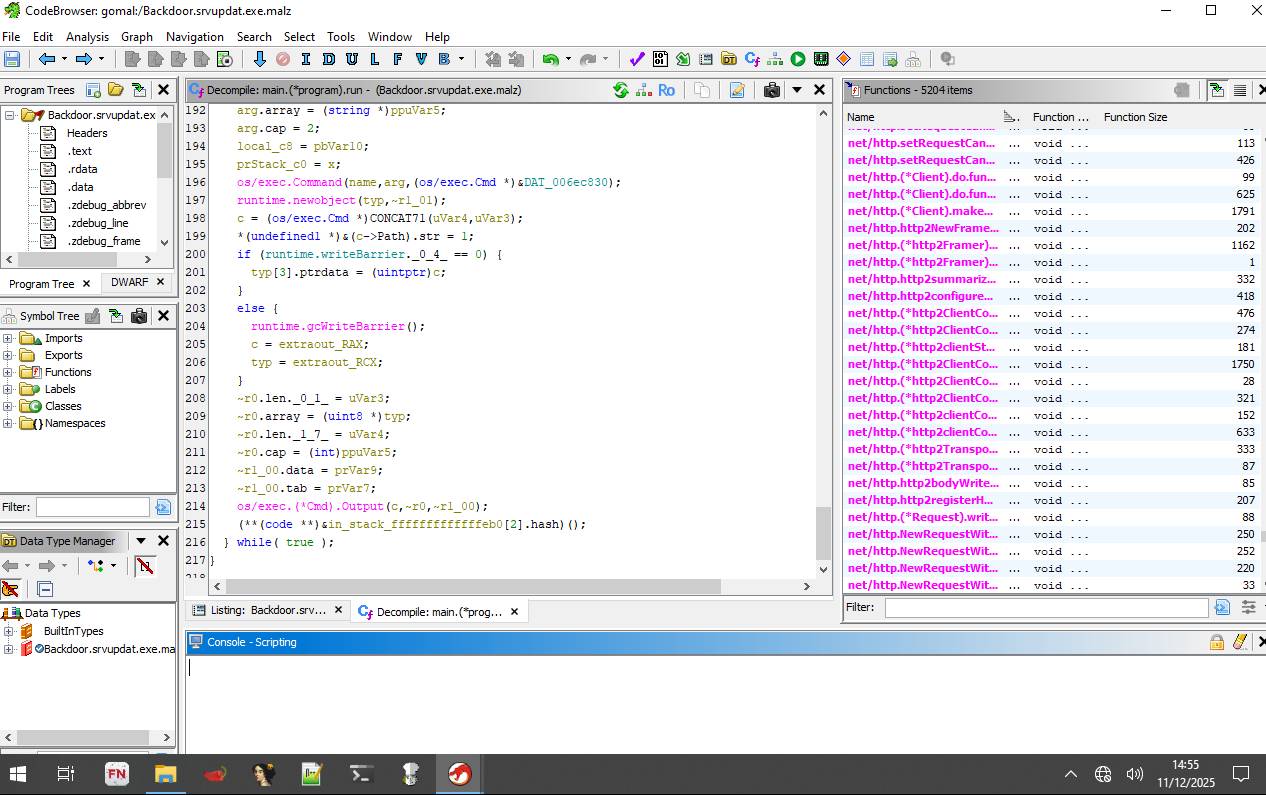 Figure 6: Decompiled GoLang function main.program.run in Ghidra
Figure 6: Decompiled GoLang function main.program.run in Ghidra
Advanced Dynamic Analysis
Indicators of Compromise (IOCs)
Host-based
- Command execution: \??\C:\Windows\system32\conhost.exe 0xffffffff -ForceV1
Network-based
- HTTP GET request to http[:]//ec2-3-109-20-24-srv3[.]local/favicon[.]ico
- Reverse shell connection to 10[.]10[.]1[.]237:3301 over TCP
- DNS requests to .local domains:
- remnux[.]localdomain
- salt[.]localdomain
- masterofmasters[.]localdomain
VirusTotal Analysis
| Attribute | Details |
| Detection Ratio | 35/72 |
| First Submission Date | 2021-12-15 16:41:32 UTC |
| Latest Submission Date | 2024-09-06 02:56:30 UTC |
| Community Comments | Detections indicate generic malware names |
| Related Indicators | ec2-3-109-20-24-srv3.local,10.10.1.237:3301 |
YARA Rule
Appendices
Appendix A
YARA Rule
rule revshell_srvupdat { meta: last_updated = "2026-01-06" author = "ScriptMissy" description = "A YARA rule for the revshell.go backdoor" strings: $gobuild = "3RKTvI30Uc68A_c6-sMB/uAW0VxD6KHkdILq2izWY/BG7xKfK9Q2QEBRq4rzpy/NCZHQC83zX7VfgJHmlhZ" ascii $url = "http://ec2-3-109-20-24-srv3.local/favicon.ico" $embedded_ip = {31 30 2e 31 30 2e 31 2e 32 33 37} $mod_name = "revshell.go" ascii condition: uint16(0) == 0x5A4D and all of them }
Appendix B
Further Research Avenues
- Double check EventCreate.exe
- Double check for RSA public key usage
TODO
- Complete advanced dynamic analysis section
- Compile full list of IOCs for Appendix B
- Check out the .localdomain DNS calls